Harassment and Phone stalking crime report
Attacks come in form of speech talked over any music or sounds output by phone including preinstalled media sounds such as phone notifications, alarms and phone ring.
I have reported this crime online sometime in spring 2016, before covid pandemic, as credit card fraud because speech was threatening to steal and use my credit card numbers and asked me where money is at. There was no follow up and nothing was investigated. I have reported this crime on 08/24/23 to Seattle police. Police officer G Wilco (#8762) gave me business card with incident number 23-244216. Oddly enough he suggested to buy new cell phone and sim card.
Perpetrator has overwritten voicemail box audio messages downloaded to my device from my telecommunications provider.
Perpetrator has been able to talk over on-hold cueue music played when i make phone calls and line is busy and i am waiting for next available representative.
Perpetrator has been able to talk over my music mixing sessions.
Thus, all recorded mixing sessions created by me with mixing software on my phone have been vandalized. It is easy to hear perpetrator talk over my music.
Any hearable audio played by my phone or tablet in form of music, sounds or voice messages played through speakers on my phone or tablet have had speech talked over.
Resulting audio contains cruelty to animals, people and nonsensical derogatory comments/remarks or stories. Attacks are aimed at me personally.
Perpetrator addresses me by my name.
Perpetrator uses my relatives names.
Perpetrator uses my friends names.
Perpetrator uses my classmates names.
I attempted to isolate Internet source of these attacks by running two simple tests.
First, I tried to remove SIM card(s) from SIM slots on my devices to see if this can stop attacks. Perpetrator has been able to talk over music played by device without SIM card.
Second, I used library desktop at international district branch to download songs i purchased from online music distributor sites. Then, i played downloaded songs with music player installed on same library desktop. Perpetrator has been able to talk over music i played at library.
I attempted to isolate Internet source of these attacks by running two simple tests.
First, I tried to remove SIM card(s) from SIM slots on my devices to see if this can stop attacks. Perpetrator has been able to talk over music played by device without SIM card.
Second, I used library desktop at international district branch to download songs i purchased from online music distributor sites. Then, i played downloaded songs with music player installed on same library desktop. Perpetrator has been able to talk over music i played at library.
Perpetrator is using government equipment to commit crimes.
There is more about content of everything said by perpetrator. I am naturalized citizen. My first language is Russian. Bulk of speech talked over my music or sounds played by my devices is in Russian. I have been able to record and save (mixcloud or soundcloud) more than enough audio artifacts most of which contain nonsensical speech in Russian. Though former coworker names pinpoint corporate disclosure. Former classmates names have been aquired from ethnic website known as odnoklassniki (classmates). It is foreign information from foreign website. It is still private information.
There is more about content of everything said by perpetrator. I am naturalized citizen. My first language is Russian. Bulk of speech talked over my music or sounds played by my devices is in Russian. I have been able to record and save (mixcloud or soundcloud) more than enough audio artifacts most of which contain nonsensical speech in Russian. Though former coworker names pinpoint corporate disclosure. Former classmates names have been aquired from ethnic website known as odnoklassniki (classmates). It is foreign information from foreign website. It is still private information.
I have reported this crime online sometime in spring 2016, before covid pandemic, as credit card fraud because speech was threatening to steal and use my credit card numbers and asked me where money is at. There was no follow up and nothing was investigated. I have reported this crime on 08/24/23 to Seattle police. Police officer G Wilco (#8762) gave me business card with incident number 23-244216. Oddly enough he suggested to buy new cell phone and sim card.
On 08/29/23 I reported this crime by phone to FBI. While I was waiting for next available agent, on hold cueue music was talked over by perpetrator. I have reported aforementioned information. Call center agent said it will be documented and suggested to report cyber crime at Internet Crime Complaint Center (IC3). ic3.gov On 08/31/23 I have submitted complaint at IC3 and added printed pdf copy of report to my documents.
On 09/08/23 I repoted this crime to Interpol and included link to this report.
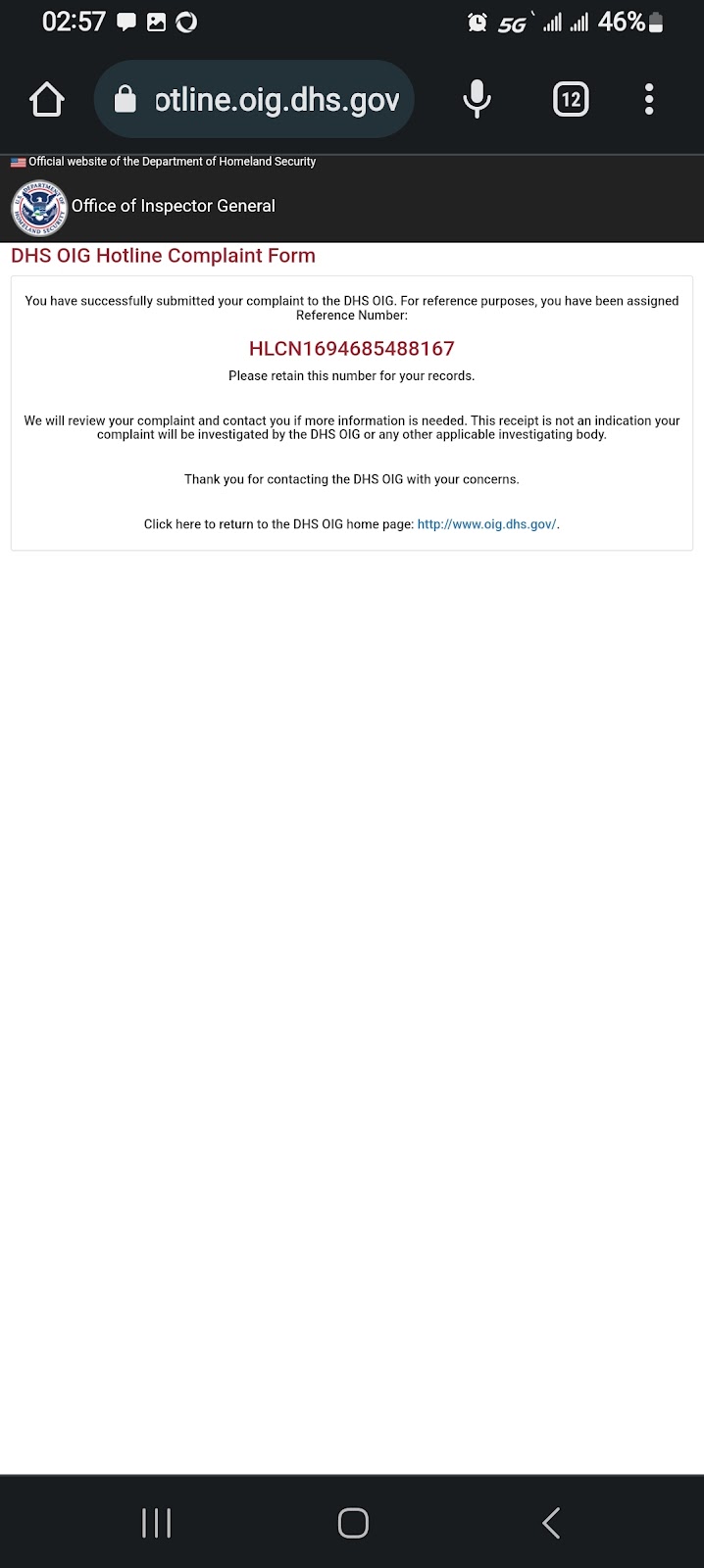
On 09/14/23 I reported employee misconduct to NSA via OIG Hotline Online Complaint Form.
On 09/14/23 I reported crime information to CIA. I included link to this report.
On 09/14/23 On 09/14/23 I reported employee misconduct to DHS Cybersecurity and Infrastructure Security Agency (CISA) online using DHS OIG allegations form.
Sat November 25th contacted national TV King 5 Investigators and Q13 Fox Spotlight. Lets see if anyone wants to investigate and report this crime. There are two more stations to contact komo 4 and kiro7 news.
I do not know who perpetrator is. Based on my sad experience these persons tend to hide. One is across Internet pipe and another running 24/7 audio bridge in buildings around me (Local manifestation of same problem), but problem is same. I am hoping FBI will investigate it as long as court requests it. I have reported this crime to police and FBI, but nothing other than incident numbers and tips piled up. I have more than one incident number from police. FBI will confirm my name with corresponding crime report (FBI calls it tips). The way I understood pdf from superior court website explaining different types of civic orders i dont have to know person who is harassing me in order to submit petition for antiharassment protection order, it will be investigated. DOJ's investigative arm is FBI and court will ask FBI to investigate it.
Besides incident numbers and tip reports, I have two letters (got those on 12th week, in March 2024) from two musical instrument manufacturers confirming 911 subsystem is not part of their products and advising me to contact attorney. As I said perpetrator talks over all music and sounds generated by my phone, tablet and now music mixer. Perpetrator was able to talk over my music mixing session involving two musical instruments connected by cable and no internet connection whatsoever.
Because mixer and speaker I own are least likely to have out-of-band 911 law enforcement subsystem and both musical instruments are under manufacturers warranty, I contacted manufacturer technical support for mixer (denon primego) and speaker (gemini sosp-8) requesting to confirm existence of 911 subsystem in their products. Gemini and Denon technical support stated in writing 911 subsystem is NOT part of their products and suggested me to contact attorney.
All phones and tablets have 911 subsystem - Its been enabled by Patriot act. It means that without telecom provider SIM chip inserted into SIM chip slot, powered phone can be accessed using 911 infrastructure. Moreover, if phone shuts down due to drained battery (0%) and battery is not removed, there is still enough energy in battery to keep 911 subsystem working. It is useful for tracking and recovery purposes so aerial drones can lock on it.
I have used phone and tablet to mix music and I have piled up many mixed music recordings with perpetrator talking over since 2015. Then I lived in Portland, OR, working for Intel Corporation as contractor and thats when I noticed perpetrator first time talking nonsensical things over songs from album I purchased and played on my android phone.
I do not know any persons who are harassing me as well as perpetrators dont know me personally but somehow, besides nonsensical rubbish, perpetrators talk coins my name, names of my friends, coworkers and classmates. Thats how I know it is targeting me.
Beyond phone perpetrator, same type of information and language is used in local manifestation of the same problem. (Electronic harassment) It is played at me in form of low frequency (recordable) audio from five businesses around where I live. Same type of intelligence being leaked out suggests same source it came from. I do not know who is doing this but I know where it comes from exactly. There are five businesses attempting to harass me quietly. I have at least two videos you can hear offensive audio coming from its premises. 1. city of seatle premises - garage behind justice center on 6th and cherry, seattle municipal tower garage on 6th and cherry, 2. Zindorf apartments 3. 7th and james apartments 4. Columbia center tower 5. Polyclinic on madison and 7th
To employers on internal threats. These fellows are like body lice. Here is simple taxonomy. One drinks your blood, two drink your blood and procreate, three drink your blood, procreate and try to rock on your dime. Gotta act up on entire population present.
Thoughts on automation. Its programmed behavior responding to your voice, besides talking over music, is to pretend it is a single person or group of people. For instance, it announces it is Dimitry Verkholashin and uses my voice. Another instance, it identifies itself as 'trenta virus'. Scanning for viruses returns summary stating devices have no viruses. Another example, it annouces it is US NAVY. I find artifacts in form of audio files. First with word 'sonar' in its file name probably tries to reproduce what real sonar sounds like. I had no clue what sonar is so I had to look it up. Second had unintelligible name and sounded like engine room on vessel or submarine. Techno sometimes sounds like it is engines of spaceship and I mixed in these two files into mixing session to compare vision of artists and whats in those artifacts. It is too real - third count of treason. Recorded sounds of real machinery can be obfuscated in electronic music tracks and then egressed to leak sites.
Thoughts on federal audit. So far these fellows had been able to slip through cracks of federal audit. I dont think anyone in the right mind will have shop with root/admin access to consumer smart devices through OOB 911 law enforcement subsystem unaudited because it will be the one to fool them. In terms of system design it means placing proper measures and mechanisms help detect malicious activity from internal threats. In well designed system such detection is automatic. I think whoever designed current system deliberately omitted placing proper measures and mechanisms to avoid detection by audits and create loopholes in system for further exploits. I have to think about storage and backup for my growing mp3 music file collection. It is about 10 gigabytes compressed. Compressing those wont yield much so there is giant proxy server instance with large number of music files constantly permuting used for staging. Traffic from my smart devices goes through same proxy just as traffic from computer lab desktop i use at library. There are technicians operating software, maintaining automation and carrying out other technical tasks using 911 infrastructure, their manager, and manager's manager. Thats power hierarchy of 'federal treasonballs rackets inc'. Im estimating it charges 50-60k per year per person, and runs its services on tiny fraction of population (5-6k people). You gotta be able to sell this service to other crooks that can afford it and there has to be environment to sell it (like sports club with racket ball rooms). Im definitely interested in their list of customers. Business line managers, government line managers and gangsters who are interested in your or your relatives professional activity are the ones who purchase this service and give your name along with cash to federal crooks. First name and last name is enough and someone who dished out that much money per year per person sure will come up with more cash to renew service subscription(s) and wont even ask you if its okay to borrow your name for that. Trying to blackmail anyone on list of customers will be stupid thing to do. You wanna do something else and thats what i am interested in. Whoever set you up is either on list of customers or someone who works for one on list of customers. This pal is in your, your relative or significant other phone book. From technical perspective pal who hooks you up with 'line to Babylon' is real person. That is, phone call is not placed by machine (prank bot) to leave message on answering machine (my voicemail). For example, if last time person was seen used strangers phone to call me, and phone from which phone call was made did not block its phone number, to me, as i look at phone calls log, it appears as phone number from which someone called me rather than unknown number, and most likely, even if no message was left, real person called me using other real persons phone.
Thoughts about our feathered friend unz with smooth federal federal connection, the guy who is still fucking with our music. He or she wanted to be tenderly called 'унцихь', and said he/she had been doing it since 2014. I noticed/heard this first time in 2015 when I was in Portland. Then I had ICE (Intel Corporation Contract Employee) job at Intel Hillsboro, OR. I moved to Portland, OR from Huston, TX where I did not want to stay at my parents place any longer and accepted job offer without relocation benefits at KAVI (Portland, OR) The question is who hooked me up and where and who has been paying for it up until now. You see its not cheap, im estimating 50 -60K per person per year. List with five thousand people will bring 30 million dirty cash every year. Who will justify operational expense like this? That is, besides me paying taxes, whose operational expense it was. Money is what keeps bitch going on. Unz won bullshit first second he started doing. Unz may have gotten away for this if he lived in country thats not free. Unz has forgotten why his ancestors came to this country. What really made unz screw up his career other than serial killer mentality. What sort of changes occured in unzes life besides improving credit. Imagine unz tries to justify his existence, budget and expenses to purchase foreign information from agents of foreign power introducing themselves as hackers for illegal purposes, this being setup in dark web where only government spies go but in reality is in person cash for data in Russia deal. Who does unz work for? Who recruited unz?
Thoughts about this whole experience. Think of buzz words 'big data'. 'big data' wont be popular buzz words anymore. I had no plans to become musician but techno always has been good to me, and, as a matter of fact, it is the best thing that has ever happened in my life and took off while I did not believe in it much and thought it was going to phase out. What gives... now some fellow is paying another fellow to thwart my efforts, first tries to hinder my success in computer industry and now same fellow tries to stop me from developing as artist. Seriously? I could be worst douche bag and schmoozer, but id never be able to convince you I work for you and we party and celebrate it by playing back to back set to your coworkers who think you are cool and have uncompromised integrity. You empowered me to tell you: you k
now me better than my mom does. Tear up, unz... Resistance is useless
Sat June 22 2024 submitted tip with link to CNN investigations.












Comments
Post a Comment